Don’t plug that into your computer – USBValve
One should never plug their phone into public chargers and devices (hotel clocks, gym machines, airport chargers, or things left laying around at hacker’s conventions…). This kind of attack is called Juice Jacking and has already been demonstrated for well over a decade. Innoculous looking charging devices, gym plugs, and hotel clocks can install malware, viruses, and steal data off phones and devices.

The OMG Cable from Hak5 was designed for exactly this. What looks like an innocent cable actually contains wifi that can be remotely controlled to act like a keyboard, log all keyboard activity, create a bi-directional network connection to control the system, and even self destructs if detected.
They also make the famous RubberDucky that you plug in and can delivery and copy data mercilessly. It acts like a normal keyboard, but by injecting simple pre-recorded commands it can direct the computer to do anything anyone sitting at the keyboard can do – including copying all your critical data to the device and walking away with it.
Protection from USB injection
Portapow creates a number of data blockers that allow you to use public USB charging ports by an adapter that physically removes the data lines. You can use them to charge devices, but they physically cannot transfer data.

Hak5 also makes a version called the malicious cable detector that detects all the currently known malicious cables.
But what if you do need to check the contents of a drive? Enter USBValve.
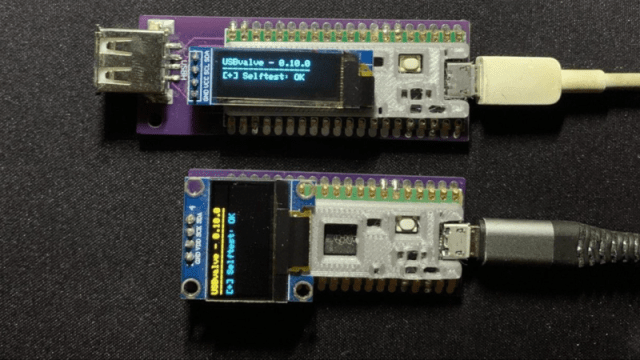
USBValve has an onboard microcontroller advertise itself as a storage device, pretending to have a filesystem with some common files available. When an unknown USB device is first inserted into the USB port on the USBValve tool, USBValve displays usage information, via the attached OLED screen, on whether the USB device is accessing files it shouldn’t be or immediately trying to write to the filesystem, which is a clear sign of malicious behavior.
This gives you access to a bunch of the lowest level debug – but likely requires a LOT of work and knowledge to use safely. It’s unlikely to be safe against hardware attacks, but it does give you something that you can potentially blow up cheaply before you plug it into a real system.
Articles: